Solutions
Eagle Cyber Shield's Solutions : Robust, Reliable, Ready for Any Threat.
Eagle Cyber Shield's Solutions: Overview
Eagle Cyber Shield provides a full spectrum of cybersecurity solutions designed to protect organizations from evolving digital threats. Our services cover every layer of security—from advanced threat detection and vulnerability management to data encryption and secure access control. By leveraging the latest in AI-driven analytics and industry best practices, we ensure that your systems are monitored, fortified, and resilient against both internal and external attacks.
We understand that every business has unique security needs, which is why our solutions are fully customizable and scalable. Whether you're a startup, SME, or large enterprise, our team of cybersecurity experts works closely with you to identify vulnerabilities, implement tailored defense mechanisms, and maintain compliance with regulatory standards. With Eagle Cyber Shield, you don’t just get protection—you gain a strategic partner committed to your long-term security and success.
Partnering with Eagle Cyber Shield means gaining a trusted advisor committed to your long-term success. We not only defend against cyber threats but also empower your team with ongoing training, awareness programs, and compliance support. Our mission is to deliver peace of mind through security excellence—so you can focus on innovation, growth, and delivering value to your customers.
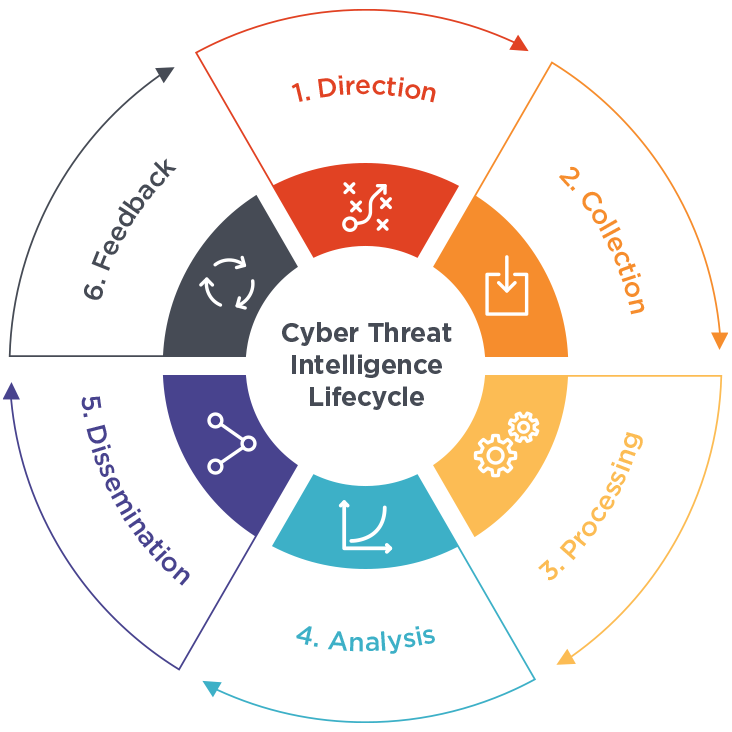
Threat Intelligence
ECS provides proactive threat intelligence solutions to anticipate and mitigate cyber threats before they impact your organization.
Eagle Cyber Shield (ECS) provides proactive threat intelligence solutions designed to identify, analyze, and mitigate cyber threats before they can disrupt your operations. Our threat intelligence system continuously monitors global threat landscapes, collecting data from a wide range of sources—including dark web forums, malware repositories, hacker activity, and open-source intelligence—to deliver real-time insights tailored to your organization's risk profile.
By leveraging advanced analytics and machine learning, ECS turns raw threat data into actionable intelligence. This enables your security team to anticipate attacks, strengthen weak points, and make informed decisions with speed and precision. Our threat intelligence solutions not only detect indicators of compromise (IOCs) but also reveal emerging tactics, techniques, and procedures (TTPs) used by threat actors. This empowers you to proactively adjust your defenses, ensuring resilience against zero-day vulnerabilities, phishing campaigns, ransomware attacks, and nation-state threats.
With ECS’s threat intelligence, your organization moves from a reactive stance to a proactive security posture—reducing response times, minimizing risk exposure, and safeguarding your most critical assets.
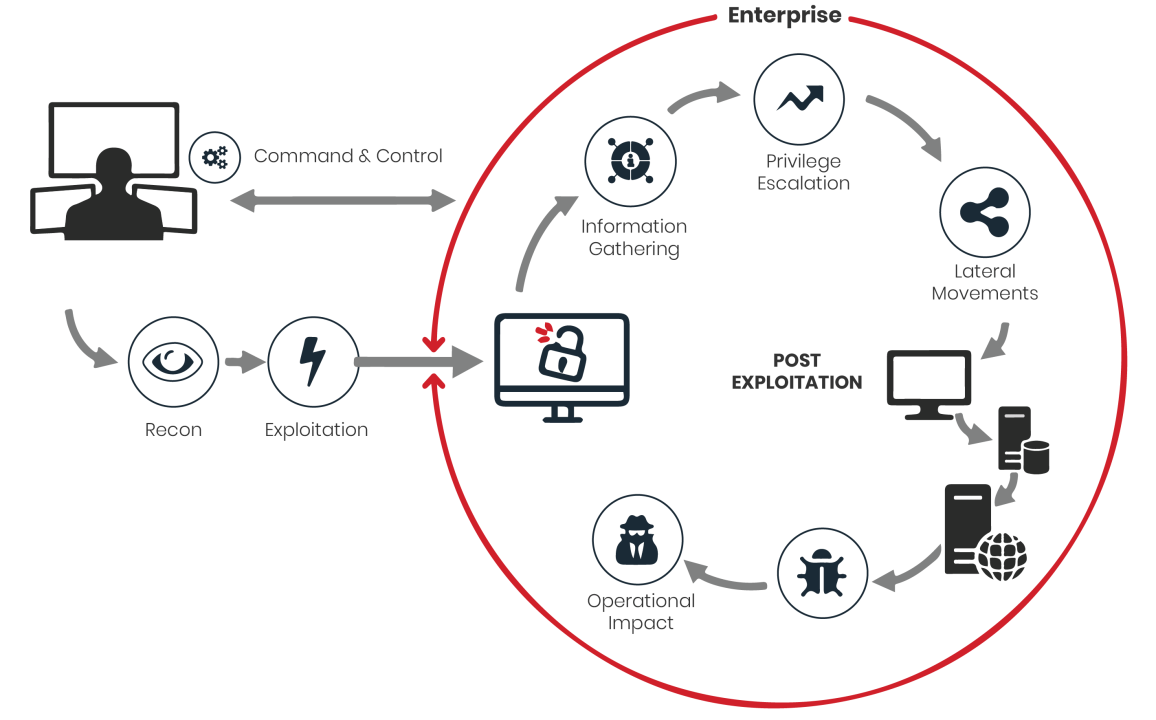
Red Team VAPT, WAPT, and Penetration Testing
At Eagle Cyber Shield, our expert Red Team specializes in simulating real-world cyberattacks through comprehensive security assessments, including Vulnerability Assessment and Penetration Testing (VAPT) and Web Application Penetration Testing (WAPT). These controlled, strategic engagements are designed to uncover weaknesses across your network, applications, and infrastructure—before malicious actors do.
Our Red Team adopts the mindset and tactics of real attackers, using advanced tools and methodologies to probe your defenses, exploit potential vulnerabilities, and assess the effectiveness of your security measures. Through VAPT, we evaluate your internal and external networks for known and unknown vulnerabilities. WAPT, on the other hand, focuses specifically on your web applications—testing for flaws such as SQL injection, cross-site scripting (XSS), authentication bypasses, insecure APIs, and other OWASP Top 10 threats.
Blue Team SOC and Vulnerability Assessment
Our blue team operates a Security Operations Center (SOC) to monitor, detect, and respond to threats, alongside comprehensive vulnerability assessments to strengthen your defenses.
A Blue Team in a Security Operations Center (SOC) is responsible for defending an organization's networks and systems against cyber threats. Their tasks include monitoring network traffic, detecting potential threats, responding to incidents, and conducting forensics to understand how attacks occurred. The team also manages vulnerability assessments, ensuring systems and applications are secure by identifying and addressing weaknesses before they can be exploited. Key tools used by Blue Teams include SIEM systems for monitoring, firewalls and IDS for traffic inspection, and EDR solutions for endpoint protection.
Vulnerability Assessment is the process of identifying, analyzing, and addressing security flaws in an organization's infrastructure. It typically involves using tools like Nessus or OpenVAS to scan for vulnerabilities, prioritizing them based on severity, and implementing remediation steps like patching or configuration changes. Regular vulnerability assessments help ensure that known security gaps are closed, reducing the risk of cyberattacks. By continuously evaluating and addressing vulnerabilities, organizations strengthen their defense against exploitation and enhance their overall cybersecurity posture.
Cloud Security
We provide IAM (Identity and Access management), DLP (Data loss prevention), SIEM (Security Information and Event Management), Business Continuity and Disaster Recovery Solutions.
Cloud Security refers to the practices, technologies, and policies designed to protect data, applications, and services hosted in cloud environments. It involves safeguarding cloud-based systems from cyber threats, ensuring compliance with regulations, and maintaining data privacy.
Cloud security also extends to managing shared responsibility models, where cloud service providers (CSPs) secure the physical infrastructure and the customer secures their data and applications.
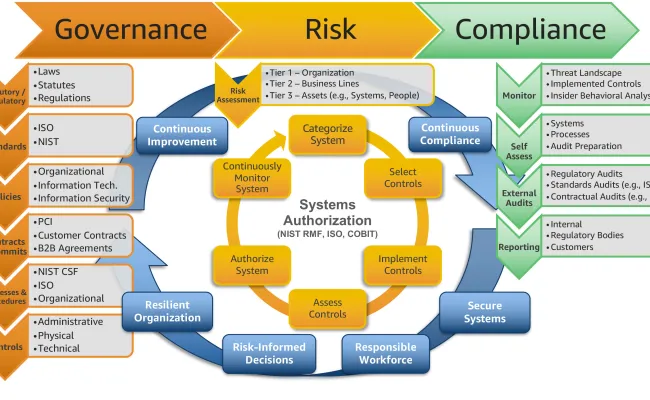
Governance, Risk, and Compliance (GRC)
ECS helps organizations establish strong governance frameworks, assess risks effectively, and ensure compliance with industry regulations.
Governance, Risk, and Compliance (GRC) is a strategic approach that helps organizations align their IT and business objectives while managing risks and ensuring adherence to regulatory requirements.
ECS (Enterprise Cybersecurity Solutions) supports organizations in building robust GRC frameworks by enabling them to identify and evaluate potential risks, implement effective controls, and monitor compliance with laws and industry standards such as GDPR, HIPAA, and ISO 27001.
Digital Forensics
In case of a breach, our digital forensics team can analyze incidents, recover data, and provide insights to prevent future occurrences.
Digital Forensics involves investigating cyber incidents to uncover how breaches occurred, what data was affected, and who was responsible. It helps in analyzing evidence from digital devices and networks.
In case of a breach, our digital forensics team recovers lost data, identifies the source of the attack, and provides actionable insights to prevent future incidents, ensuring swift and secure incident response.
Cryptography Solutions
We offer advanced cryptography solutions to secure sensitive data, ensuring confidentiality, integrity, and authenticity in communications.
Cryptography Solutions protect sensitive data by converting it into secure, unreadable formats that can only be accessed by authorized users. It ensures data confidentiality, integrity, and authenticity across digital communications and storage.
We offer advanced cryptography solutions including encryption, digital signatures, and secure key management to safeguard critical information. Our services help prevent unauthorized access, data tampering, and ensure secure communication across systems and networks.
Eagle Cyber Shield Technologies: Solutions
Our Solutions can help you with Vulnerability management, monitor and audit container activity.